Legacy Email Authentication
Effective 9 August 2021, legacy email clients and services that do not support 2-Factor Authentication (2FA/Duo) no longer function to send or retrieve UC Merced email. To learn more, visit our web page detailing the reasons for the change and the impact it may have on you: https://it.ucmerced.edu/Legacy_Auth_Changes.
Cybersecurity Matters
In this space, we will look at the rapidly changing cybersecurity landscape, how it is impacting our personal and professional lives, the challenges we face, and what we can do by following best practices, cyber hygiene, and prevention strategies.
Advanced Persistent Threat (APT) Attacks
An Advanced Persistent Threat (APT) is a multi-phased attack on an organization’s network. It typically features a strategic, prolonged and continuous attack on the network with a goal of gaining entry to that network while avoiding detection. Once attackers gain access, they are persistent, patient, and coordinated in continued attacks. This is what makes APT different than traditional threats.
APT Attack Motivations
Higher Education is a potential target for APT attacks due to its ties to education, research, healthcare, and government. APT attackers that target higher ed are typically attempting to spy on the organization, make money, or create chaos.
- Goal: Espionage
APT attacks can sometimes be perpetrated by nations/states based on their national interests. Developed nations/states have cyber groups whose goal is not only to defend but also to attack the other countries' infrastructure and industry, e.g., healthcare, education, energy, and transportation. - Goal: Financial Gain
Corporate or industrial espionage-driven APTs typically involve stealing, blackmailing, and defrauding people and corporations. - Goal: Creating Chaos
APT attacks with the goal of creating chaos are usually perpetrated by well-funded hacktivist groups. Such groups may be anti-capitalist, anti-socialist, anti-establishment, or anti-government in nature.
Specific Targets:
- Organizations like government branches may have sensitive data on their servers. APT attacks often target this sensitive data, which can be used for exploiting further attacks, creating chaos in a country, or weakening the government.
- Access credentials in the server are one of the most lucrative assets for an APT attack. APT attackers use high privilege credentials, which can cause significant damage to an organization.
- Personally, Identifiable Information is also one of the targets of an APT attack. Personal information such as names, addresses, credit card purchase records, etc. can be used by major industries for devising a strategic plan.
- Intellectual property (patents, designs, trade secrets) are heavily guarded digital assets. APT attacks often target these assets because they can give a competitive advantage over one company to another.
APT Cyberattack Lifecycle
The APT cyberattack lifecycle refers to the operation, processes, tools, and techniques attackers use. It consists of a series of steps:
- Reconnaissance and Research
During this stage, attackers gather all possible public information about a targeted organization and study its workflow. They use social media platforms such as Facebook, Twitter, LinkedIn, and Instagram to obtain information about individuals and organizations.
- Weaponization
During the weaponization stage, attackers generate an attack strategy based on the knowledge obtained in the reconnaissance stage. Attackers combine an exploit with a payload.
- Delivery
Delivery is the deployment of the payload developed during the weaponization of the targeted system.
- Exploitation and initial intrusion
Exploiting a vulnerability to access the system and initial intrusion is the first unauthorized access to the targeted system, which paves the way for all future attacks. The vulnerability will be exploited, which allows the malicious code to be executed on the victim’s system. An example would be to deliver malicious code in a .pdf file sent as an attachment via email.
- Installation
Malicious software will take over the system in this part of the cyberattack lifecycle. Once the malicious code from the PDF is on the computer, the attackers can install and run the code.
- Command and Control
This part of the cyberattack lifecycle involves taking control of the compromised system by establishing remote control after the initial intrusion and deploying evading procedures. The attackers can lock you out of your accounts to allow themselves more time to work.
- Lateral movement
Lateral movement involves discovering the targeted digital assets in the system and/or on the network. Attackers can then move laterally to other systems/computers from the hacked computer and access other credentials (privileged accounts) and data.
- Action and Objectives and Extraction
Once attackers accomplish their goals and extract the data they are after, they can transfer that data to the attacker’s system. In most cases, this data is encrypted, and the users can’t use their own data. This is also called ransomware.
Phishing
Phishing is the number one threat delivery and communication vehicle in the world today, allowing cybercriminals to exploit system vulnerabilities to gain access to sensitive data, personally identifiable information (PII), and other valuable information.
In Phishing, cybercriminals have a perfect attack and delivery tool: a digital medium used by almost anyone in today’s connected world to conduct all types of real-time business that can carry any type of content, links, and attachments. It is anonymous, has a marginal cost to use, and is one of the most common services offered by the service providers. Simply put: If you have an email address, you are a target. So, you must be prepared.
What is Phishing
Phishing is defined by the Oxford Dictionary as, “the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers”. In layman’s terms, a Phish is an email that is designed to look like it came from someone else, to steal or obtain personal information on you. While attacks can come in many shapes and forms, here are a few of the most used phishing attacks you’ll see today:
The Big Phish A.K.A. The Usual
The typical spam attack. Hundreds of thousands of emails were sent to people with the hope of getting just a few people to click on them. Often poorly formed, filled with spelling errors, and typically demanding you respond to them right away OR ELSE, this kind of spam is the most common, and the most annoying.
Spear Phishing
Instead of a big spam attack spread over hundreds of thousands of people, a “Spear Phish” targets a small group. These kinds of phishes usually are addressed to a specific individual with the hope of obtaining sensitive information or getting the recipient to perform an action, such as purchasing Amazon gift cards.
Business Phishing
Business Phishing is a generic term for any kind of Phish that looks, sounds, or acts like a regular business request, such as requesting a quote or a question from a supplier. These kinds of phishing may ask for seemingly harmless information but are using it to gain your confidence and get information, and data that might be used in other crimes.
Whaling
Whaling is a very specific kind of phish targeted at the heads of departments, groups, or even entire organizations. A Whaling Phish would be well crafted and seem to come from trusted sources, such as other universities or important businesses, fooling their target into a false sense of security, allowing them to gain their trust and eventually, compromise their system or even encrypt it and hold it for ransom.
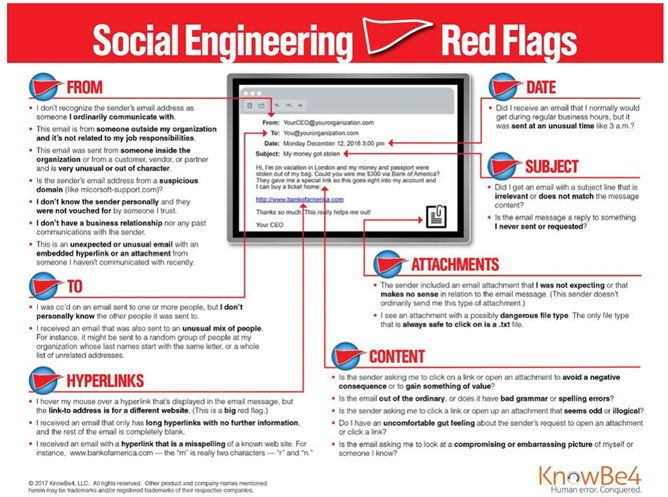
How to spot a phish
So now that you know some of the more common phishes out there, how can you recognize a phish when you see one? It’s easy to spot a phish when you know what to look for. Check out the UC Merced IT Phishing Archive, found at (https://it.ucmerced.edu/phishing). Below are a few ways you can spot a phish:
-
Too Good To Be True – Any offer too good to be true usually is, and cyber criminals use offers that sound wonderful to get you to respond to their requests, usually for a credit card or other personal information. Take everything you read on the internet with a healthy dose of skepticism, and if something sounds like it’s too good to be true, it probably is.
-
Sense of Urgency and Use of Emotions - A favorite tactic amongst cybercriminals is to ask them to act fast because the super deals are only for a limited time. Some of them will even tell you that you have only a few minutes to respond. Sometimes they will tell you that your account will be suspended unless you update your personal details immediately. When in doubt, pick up the phone and call!
-
Hyperlinks – Those Big Blue Hyperlinks in a document can be manipulated to go anywhere they want, regardless of the actual link displayed. This link here that says http://www.google.com will take you to Amazon if you click on it, and the same can happen in an email. Cybercriminals fool you into thinking an email is legit, but instead, when you click on the link, you’re taken to a webpage where malware is installed, and your system is encrypted. You can hold your mouse over the hyperlink to display where the link is going: Before you go anywhere, know where you’re going first!
-
Attachments – A phisher may masquerade as a trusted friend or coworker and send you an email with an attachment, claiming it’s a picture or asking you to look at their resume, but the attachment is instead a file designed to hijack your system. If you were not expecting an attachment, don’t open it. Contact the source and verify they sent the file before double clicking on that attachment.
Here’s a good example of a phishing email.
(Click Here to download the above image)
Consequences of Phishing
The consequences and impacts of phishing are real. A phisher who steals your UC Merced Username and Password can access a variety of services on campus, potentially exposing the University and other staff and faculty members to data theft and loss or allowing unauthorized individuals access to sensitive research data. Clicking on a phishing link could grant cybercriminal access to your computer, allowing them to steal your photos or financial documents, or even your credit card numbers. They could even encrypt your computer, holding it for ransom unless you pay them hundreds or sometimes thousands of dollars.
The FBI’s Internet Crime Complaint Center reported that people lost over $54 million in 2020 due to phishing scams, and as time goes on things will only get worse. You need to protect yourself.
How to Protect Yourself from Phishing Attacks
In addition to the techniques discussed above, the best way to protect yourself from Phishing Attacks is to practice good cyber hygiene, which includes making sure your computer and anti-virus are up to date, changing your password on a regular basis, and using passphrases instead of passwords for better security. Use Two Factor Authentication when possible and enroll in a backup service like CrashPlan to protect your data, should you fall for a phish and your system becomes compromised. Above all, always be suspicious – and NEVER give out personal information. When in doubt, report the email to information security and we can help figure it out. As part of the services we offer for UC Merced, you can get our Anti-Virus, FireEye HX, and our backup software, CrashPlan, at the links below:
FireEye HX for Windows – Click Here
Fireye HX for OS X – Click Here
CrashPlan for Windows – Click Here
CrashPlan for OS X – Click Here
What To Do if You Suspect a Phish
If you receive a suspicious email, do not open the email, do not click on the links, and do not open the attachments. Contact information security at infosecurity@ucmerced.edu. Please forward any phishes you may get, even if you think others have reported the phish already. Every phish reported helps!!
What To Do if You clicked on a Phish
If you fell for a phish, don’t worry – Information Security is here to help. Email infosecurity@ucmerced.edu immediately or call the service desk at (209) 228-4357. We will help you from there.
Remote Work
For most of us working at home, either one or a few days a week is now a reality we must face. As the boundaries between home and the office blur, the remote working model expands the scope and complexity of the operating environment in higher education. One area of concern is the increased cybersecurity-related risks due to an increasingly remote workforce. Vulnerabilities created by this remote workforce are the main reasons for the increased risks due to more remote access, increased use of third-party solutions, and of course, the use of the home Wi-Fi networks.
As employees access the campus resources and network remotely, certain vulnerabilities are not as easily managed. Lack of network security controls in a home setting creates vulnerabilities, e.g., Wi-Fi networks without passwords or wireless router default admin passwords, i.e., “password”. Different types of technology devices using the same Wi-Fi network without any network segmentation could also create vulnerabilities. The use of personal devices that are not properly protected in accessing institutional resources and assets also creates vulnerabilities.
Despite our best efforts, compromised user accounts still represent the most significant risk to our networks. Phishing remains a persistent threat as well, and it represents a risk that exists no matter where employees reside. The job function, the device used, and the type of applications and data accessed by those devices determine what remote access controls need to be put in place. Human error is inevitable regardless of where you work from, but by simply maintaining good cyber hygiene and personal security best practices, we can remediate the associated risks around our personal and organizational data.
Tips to stay safe at home:
- Ensure your device is covered by an advanced Next Generation Anti-Virus and Malware detection software.
- Ensure your operating system and applications are up to date with critical vendor fixes/patches and are encrypted.
- Use Virtual Private Network (VPN) for remote access to campus resources.
- Use the cloud-based backup service and cloud-based unlimited storage for your data.
- Uninstall old programs or applications you no longer use.
- Screen-lock your devices when not in use to prevent others at home from using it.
- Make sure your settings automatically lock your device when it’s inactive for a certain amount of time.
- Home wireless routers nowadays are very user-friendly to configure/setup and make the following tasks easier, they have basic and advanced settings as well.
- Secure your Wi-Fi-network by choosing a complex router username and password.
- Enable WPA2 security from your router’s settings and allow only known MAC addresses.
- Segment your home network into zones, e.g., kids, IoT (TVs, refrigerators, lights) security cameras, guests, and work.
Ransomware
IBM Security Center reports Ransomware as the top cyber threat in 2020. During the pandemic, the number of ransomware attacks more than doubled, growing not only in frequency but also in sophistication and ransom demand. In 2020, the average demand grew to $170,000, with high-end demands exceeding $1 million. In May 2021, Colonial Pipeline, a major refined-oil products supplier responsible for 45 percent of the East coast’s fuel supply, was hit with ransomware and ended up paying $4.4 million in Bitcoin to unlock the encrypted files and get the pipeline back up and running.
Ransomware attacks are not only affecting businesses; colleges and universities are also prime targets for attacks. The FBI's Cyber Division recently warned that ransomware poses a huge risk for higher education, as cybercriminals using this type of attack are now focusing heavily on colleges and universities. According to Microsoft Security Intelligence, education is the most affected sector by malware attacks. Within the last thirty days, educational organizations have been the target of more than 5.9 million malware attacks, more than 63% of the total. The UC system is also at risk of having its data about students, employees, operations, and research encrypted by cybercriminals. In 2020, UCSF School of Medicine was the victim of a ransomware attack and ended up paying $1.14 million to recover the encrypted research data.
So, what is ransomware?
Ransomware is a type of malware. A ransomware attack is conducted by a cybercriminal to hold data hostage for a ransom, expecting payment for the data to be released. This is done by encrypting the data via a malicious computer code. The owner of all the files that have been encrypted can no longer access those files. In addition to encrypting the data and demanding payment to restore access, cybercriminals also threaten to sell or publish the sensitive data on the deep web if their demands are not met, aka Double Ransomware. Ransomware as a Service (RaaS), nowadays widely available, also makes it easier for cybercriminals to deploy ransomware in an automated fashion with the click of a button.
How does it work?
The most common attack method is not technical. The attackers are not, for the most part, using exploits against vulnerabilities to external-public-facing services. They are not breaking into web applications and pivoting from web application infrastructure into the inside of an organization’s network. Cybercriminals can gain access to an organization’s data through various means. The primary avenue for attacks today is social engineering, including phishing emails and unpatched software on user computers. Patches are issued by software companies for vulnerabilities they find in their programs; many users fail to download the patches, which means the vulnerabilities can be exploited via the malware downloaded to the computers as users click on the links or open attachments in the phishing emails. An unprotected and unpatched computer allows cybercriminals to easily compromise credentials, establish a foothold, escalate privileges, move laterally while doing internal reconnaissance, infect other computers and eventually complete their mission when they find the valuable data worth ransom. Once the ransomware has launched and files start encrypting, one of the first things a victim will notice is that their files no longer have the same extensions and cannot be opened. The user may find a text file in the Documents directory that has a name that includes words like decryption, instructions, help, restore or recover. This file will include directions on how to pay the ransom as well as a link to a site. A more immediate way of getting the user’s attention is to change the background image on the desktop indicating the ransomware.
What are the consequences?
There are tangible and intangible risks due to a ransomware attack. Cost is obviously one. In addition to the ransom amount, there might be costs associated with response, containment, restoration of services/files, remediation, forensics, notification, litigation, penalties, regulatory fines, and any other costs directly attributable to the ransomware incident. It is also likely that there will be temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, and potential harm to an organization’s reputation.
What can you do?
Bad things are going to happen, and there is no such thing as 100 percent security. In the end, it may not be possible to prevent these attacks from happening; however, being prepared as much as possible can help you/organization to respond quickly and restore your data and services. Building a culture of cyber readiness that’s resilient against these attacks requires preparation response and recovery. Preventative actions such as creating backups of critical data and testing those backups via restore processes are effective measures.
Following are the key elements to protect against and recover from ransomware.
- Prioritize your data for protection and backup purposes.
- Use the cloud-based backup services provided by OIT and make sure you can restore your data from the backups and get back to work.
- Use cloud-based unlimited storage for your files provided by OIT.
- Update your software with the latest security patches and make sure encryption is enabled for your computer. This makes it harder for malicious actors to compromise your system. OIT provides a service to manage operating system and application patches and fixes, including encryption for your computers.
- Ensure your devices are protected with an endpoint security tool, e.g. FireEye HX.
- Take advantage of Research Data Management and Research Data Security Assurance Consultation services provided by OIT.
- Use Virtual Private Network (VPN) for remote access to campus resources.
- Use 2-Factor Authentication: DUO or Hardware Token.
- Request Single-Sign-On (SSO) for services where possible.
- Change and reset your password if you have any concerns.
- Be aware of phishing emails and think twice before clicking on any link or opening an attachment in an email. Malicious actors often use phishing to infect a system with ransomware.
How do I respond to a Ransomware infection?
If you believe your system has been infected with ransomware do not panic, but DO NOT WAIT. Please act immediately, using the following steps to prevent the spread of the infection.
1. Disconnect From Networks
- Unplug Ethernet cables and disable Wi-Fi or any other network adapters.
- Do not plug these devices into anything until checked and verified by the information security or service desk.
- Put your device in Airplane Mode
- Turn off Wi-Fi and Bluetooth
- This can aid in preventing the spread of ransomware to shared network resources such as file shares. Enabling Wi-Fi or network connectivity even for a moment will allow the ransomware to spread to neighboring devices.
2. Disconnect External Devices
- USB drives or memory sticks
- Attached phones or cameras
- External hard drives
- Or any other devices that could also become compromised
3. Report the Incident
- Contact the information security team by emailing infosecurity@ucmerced.edu.
- Call the Service Desk at 209-228-HELP (4357) who can expedite connecting you with a member of our incident response team.
- Visit https://oit.ucmerced.edu and click "Report a Problem" on the right-hand side.
- Contact the owner of the equipment (researcher) and keep them informed.
Cybersecurity Challenges
In this modern world, Information and Technology (I&T) are foundational elements to every organization. I&T has driven every industry, including higher education, to be efficient and effective—and yet we are entirely dependent on technology as a result. Despite all the benefits of this change, there are also challenges and associated risks:
- The availability and rapid adoption of the latest technology—e.g., ubiquitous broadband and mobile communications, Artificial Intelligence, Machine Learning, Neural Networks, Deep Learning, Internet of Things (IoT), easy access to knowledge, and all the data we now generate—make security and privacy challenges even more complex to address
- The threat landscape and attack sophistication are growing. It is easier for threat actors to launch attacks with a single push of a key in this 24x7 connected world.
- The growing number of regulations in the cybersecurity realm highlights our need to protect privacy.
- Digitization, digitalization, and digital transformation efforts while creating more value for the stakeholders, also introduce cybersecurity risks and challenges, e.g., access management, data breach, data loss, insecure APIs, misconfigurations, and increased DoS/DDoS attacks.
- Remote work is now another reality and is here to stay with its own pros and cons. As a result, the boundaries between home and the office are blurring. Poor cybersecurity and data hygiene at the home office increases the risk of credential, data, and device compromises.
- Operational resiliency is a challenge made greater by our reliance on multi-cloud, multi-operating systems, and multi-vendor service platforms.
- Managing costs along with the scarce skills and talent.
Unlike the profit-driven private sector, higher education is particularly vulnerable to these challenges due to its open and inviting culture, which often translates into “open networks.” In such an environment, it is important to make informed, risk-aware decisions to protect our organizational assets and comply with laws and regulations. The goal is to prioritize risks without trying to address every threat or vulnerability, given our organization’s limited resources.